Yanzi Secure Edge Platform
Yanzi Secure Edge is an open building platform that allows building owners and integrators to effortly access building systems and deploy apps to them.

System components
- Secure Edge Platform: The overall name for the solution and all components.
- Secure Edge Gateway: The plug'n'scan edge device that is plugged into the building.
- Secure Edge Portal: The web portal from which you may access your edge apps and systems.
- Secure Edge Client: Access your systems from your laptop.
Included in the subscription
Included in all licenses for the Secure Edge is the following components:
- 1. Portfolio management.
-
All your systems in one place.
- 2. Secure Remote Access.
-
Access your existing and future systems.
Usage and Configuration
- 3. Single-Sign-On and role based access.
-
Single login to all systems. Self-service role-based credential management.
Configuration
Tip
Additional functionality can be unlocked by adding apps. (Separate pricing applies). Ask your key account manager about Ecopilot and apps today, or browse the application list.
Included in the box
| Note | Included | |
|---|---|---|
| SEG | Main unit | Yes |
| DIN rail | 35mm DIN rail mounting kit | Yes |
| Rack mounting | 19” rack mounting by 2U shelf | No |
| Power supply | 12-24VDC power supply required. Current consumption: 12VDC 1.21A 24VDC 0.66A |
No |
| Power connector | Flat screw terminal connector | Yes |
| Ethernet port LAN | 10/100/1000 Mbps Ethernet, isolated from WAN. | - |
| Ethernet port WAN | 10/100/1000 Mbps Ethernet, isolated from LAN. | - |
| Ethernet cable | No | |
| Power cable | No |
Installation
Needed tools:
- SmartPhone/laptop with internet capability.
- Network cables
- Flat 2.5mm screwdriver
- Power cables
- Power supply
| Step | Instruction |
|---|---|
1 |
Connect a network cable between the SEG's WAN port and the network providing internet capability by DHCP. |
2 |
Power the SEG with 12-24VDC. |
3 |
Wait 5 minutes to let it boot up. |
4 |
Sign into the portal and click the "+ Gateway" button. 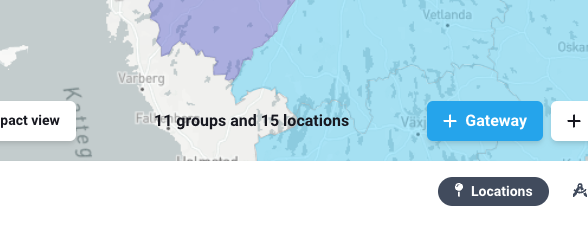 |
5 |
Follow the steps in the connection guide. (Select Other/Don't know if your gateway model can't be selected) |
6 |
Place the SEG on the map (Yanzi Lifecycle > Settings > Gateway position). |
7 |
Follow the instructions. You will be prompted to scan the QR-code on the device. |
This completes basic installation. A system will be created with you as the sole administrator - a good next step might be to add more users or configure new tunnel endpoints.
Danger
Always scan and provision the device when powered the first time. Unpeered devices can be claimed by other parties, giving them administrator access to the system and network.
Secure Remote Access
To access your remote systems, click them in the sidebar:
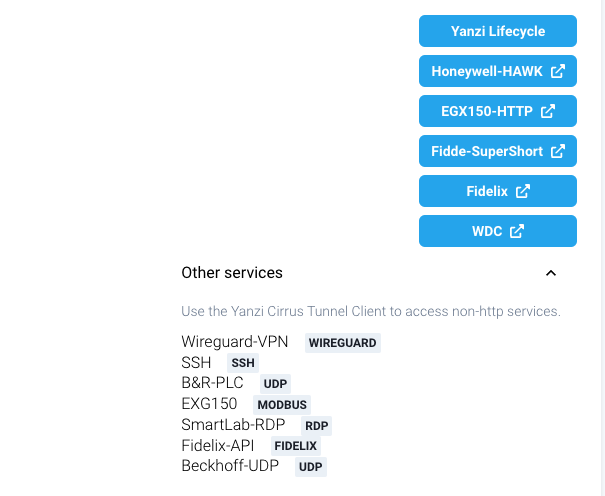
To add more tunnels, see here.
To access some tunnels, you need the Secure Edge Client.
Special Tunnel subTypes
Some Tunnel types have special behaviour:
wdc
Enables authentication with local WDCs. Sets the following headers:
| HTTP | |
|---|---|
1 2 | |
identity-proxy
Enables authentication by injecting standard reverse proxy Headers into the http requests.
Sets the following headers:
| HTTP | |
|---|---|
1 2 3 | |
stp-webfactory
Enables authentication by injecting a signed JWT with the current user data.
Sets the following headers:
| HTTP | |
|---|---|
1 | |
Structure of the jwt payload:
| JSON | |
|---|---|
1 2 3 4 5 | |
stp-atvise
Similar to the "stp-webfactory" but appends the jwt as a GET parameter named "altacognijwt" (note different spelling from stp-webfactory)
Secure Edge Client
HTTP(S) endpoints can be accessed through the Portal, but to connect to other protocols, we offer the Secure Edge Client. This is a piece of software that runs locally on your laptop.
HOWTO USE THE CTC
Limitations
- Do not use the tunnels for long-lived connections. They will be terminated.
- The tunnels will be throttled if excessive bandwidth is used.
- The tunnels can be restarted at any time due to cloud resource allocations.
If you require strong uptime guarantees, or will transfer large amounts of data, then this should be done through a traditional VPN solution or similar.
Can I use the tunnels to access api´s and stream data?
The tunnel feature is designed for remote management of systems and should not be used for programmatic access. For integrations, please use the supported API surfaces.